What is Business Email Compromise or CEO Fraud?
Cyber criminals are constantly coming up with new ways to get what they want.
Cyber criminals have developed a new attack called CEO Fraud, also known as Business Email Compromise (BEC).
- Cyber criminals pretend to be the Chancellor or other high level administrators - they send an email to faculty and staff members to trick you into doing something you should not do.
- Cyber criminals search the website, LinkedIn, Facebook etc to learn more about Appalachian State University employees and target specific employees.
- Targets are chosen based on the Cyber criminals goals, for example money, tax information, etc.
- The term Spear Phishing is a custom message targeting these select people.
- Spear Phishing is very effective because they are extremely realistic and appear to come from someone you know.
- These emails often create a tremendous sense of urgency, demanding you take immediate action and not tell anyone.
- The cyber criminal’s goal is to rush you into making a mistake.
Examples of BEC Attacks:
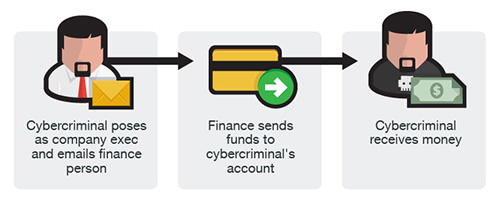
- Wire Transfer: The cyber criminal researcher who works with Appalachian’s finances. An email is sent pretending to be the target's boss. The email says there is an emergency and money has to be transferred to a certain account.
- Tax Fraud: Cyber criminals target employees in Human Resources and an email is sent from a senior executive demanding certain documents be provided immediately.
- Attorney Impersonation: Criminals may impersonate a senior leader with an email saying an attorney will be contacting you. The criminal calls pretending to be the attorney with a tremendous sense of urgency for confidential matters
Protecting Yourself Against Business Email Compromise
- Use your instinct, if it doesn’t feel right, it may be an attack
- Sense of urgency, tones, different email addresses or phone numbers can be a clue
- When in doubt, call the person at a trusted phone number or meet them in person (don’t reply via email) and confirm if they sent the email
- Never bypass security policies or procedures.
- If you receive such a request and are not sure what to do, contact your supervisor, the Help Desk (828) 262-6266, or forward the email to the Office of Information Security at phish@appstate.edu .